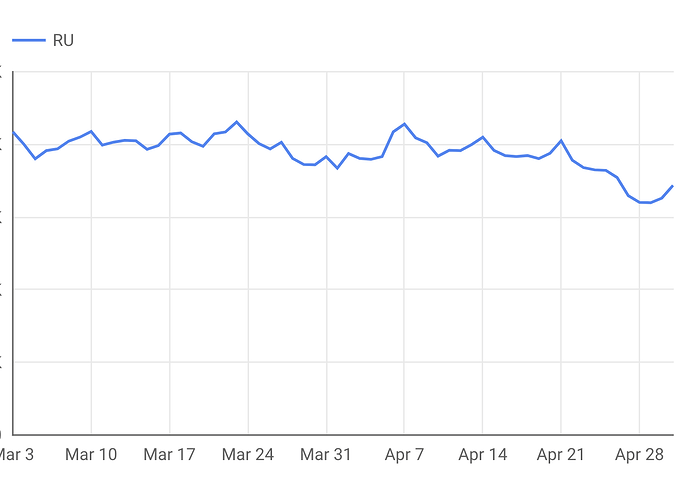Блокируют по размеру пакетов, возможно, не по абсолютным цифрам, а по соотношению размера отправляемого к принимаемому.
HTTPS-соединения устанавливаются 1 раз из 6-7 (в дампе все неудачные), а HTTP устанавливаются всегда (у них другие размеры пакетов).
shadowsocks-block-tele2-29.04.2024.pcapng (44.7 KB)
Очень похоже на Случайная блокировка игры SCP Secret Laboratory на ТСПУ по UDP протоколу - #28 by ValdikSS
Без обсуждений.
Обсуждение в Обсуждение: неработоспособность ShadowSocks (30.10.2023+)
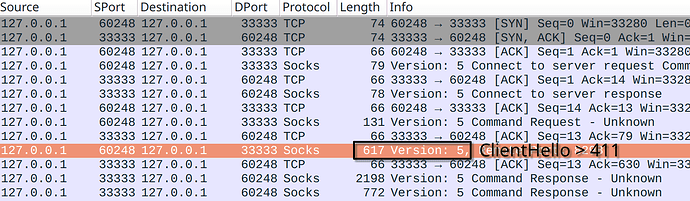
Нашел как минимум один шаблон блокировки (для TCP):
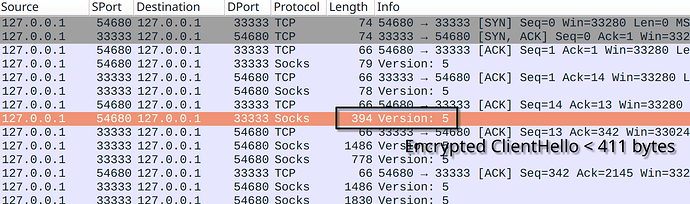
- Клиент отсылает три пакета, каждый из которых содержит 411+ случайных байт
- Сервер отсылает произвольное количество любых байт чаще, чем клиент отправляет свои пакеты
Where was your test network?
Remote Testing with the Outline SDK
You can use the Outline SDK Tools to test different strategies remotely.
Here I test a fetch from Bee Line:
go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE" https://ipinfo.io/org
AS16345 PJSC "Vimpelcom"
$SERVER_BEELINE is a socks5://... url pointing to a SOCKS5 server running on Bee Line.
Here is a blocked website:
go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|override:host=cloudflare.net" -method HEAD -v https://meduza.io
2024/04/29 15:49:50 HTTP request failed: Head "https://meduza.io": EOF
(I’m using override to bypass DNS blocking)
TLS Record fragmentation bypasses blocking:
go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|override:host=cloudflare.net|tlsfrag:1" -method HEAD -v https://meduza.io
[DEBUG] 2024/04/29 15:50:35.534519 main.go:106: Expires: [Mon, 29 Apr 2024 19:51:05 GMT]
[DEBUG] 2024/04/29 15:50:35.535194 main.go:106: Alt-Svc: [h3=":443"; ma=86400]
[DEBUG] 2024/04/29 15:50:35.535205 main.go:106: Cache-Control: [public, max-age=30]
[DEBUG] 2024/04/29 15:50:35.535211 main.go:106: Last-Modified: [Mon, 29 Apr 2024 19:25:15 GMT]
[DEBUG] 2024/04/29 15:50:35.535215 main.go:106: Cf-Cache-Status: [HIT]
[DEBUG] 2024/04/29 15:50:35.535220 main.go:106: X-Content-Type-Options: [nosniff]
[DEBUG] 2024/04/29 15:50:35.535225 main.go:106: Date: [Mon, 29 Apr 2024 19:50:35 GMT]
[DEBUG] 2024/04/29 15:50:35.535229 main.go:106: X-Cg-Cache-Status: [HIT]
[DEBUG] 2024/04/29 15:50:35.535233 main.go:106: Age: [168]
[DEBUG] 2024/04/29 15:50:35.535237 main.go:106: Strict-Transport-Security: [max-age=31536000; includeSubDomains; preload]
[DEBUG] 2024/04/29 15:50:35.535243 main.go:106: Server: [cloudflare]
[DEBUG] 2024/04/29 15:50:35.535247 main.go:106: Cf-Ray: [87c1d2664d33614a-KJA]
[DEBUG] 2024/04/29 15:50:35.535250 main.go:106: Content-Type: [text/html; charset=utf-8]
[DEBUG] 2024/04/29 15:50:35.535311 main.go:106: Connection: [keep-alive]
Testing Shadowsocks
To fetch with Shadowsocks:
go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$OUTLINE_SERVER" https://ipinfo.io/org
AS14061 DigitalOcean, LLC
Where $OUTLINE_SERVER is a ss:// Shadowsocks key.
Now we can do a two-hop test by piping the transports. Here we connect to Bee Line, then fetch ipinfo.io via the Outline Server. We seem to get timeouts for HTTP:
go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|$OUTLINE_SERVER" http://ipinfo.io/org
2024/04/29 15:58:02 HTTP request failed: Get "http://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
And HTTPS:
go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|$OUTLINE_SERVER" https://ipinfo.io/org
2024/04/29 16:00:07 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
When I use a prefix that simulates a TLS Handshake Record the HTTP fetch succeeds:
$ go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|$OUTLINE_SERVER?prefix=%16%03%01" http://ipinfo.io/org
AS14061 DigitalOcean, LLC
$ go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|$OUTLINE_SERVER?prefix=%16%03%01" https://ipinfo.io/org
AS14061 DigitalOcean, LLC
Note that my Outline Server is running on port 443.
I was able to get 10 successes in a row:
for i in $(seq 1 10); do echo -n "Test $i: "; go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|$OUTLINE_SERVER?prefix=%16%03%01" https://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
But it’s not always successful. I don’t know if that’s an issue with my Bee Line being slow or if it’s inconsistent blocking:
$ for i in $(seq 1 10); do echo -n "Test $i: "; go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "$SERVER_BEELINE|$OUTLINE_SERVER?prefix=%16%03%01" https://ipinfo.io/org; done
Test 1: 2024/04/29 16:10:14 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 2: 2024/04/29 16:10:20 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 3: 2024/04/29 16:10:26 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: 2024/04/29 16:10:41 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 9: 2024/04/29 16:10:47 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 10: AS14061 DigitalOcean, LLC
I’ll see if I can test in more networks. but it would be great if others could test too.
Did some testing on Megafon:
$ go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "socks5://$SERVER_MEGAFON" https://ipinfo.io/org
AS31224 PJSC MegaFon
It’s not completely clear to me if the timeouts are blocking, or just slowness. I’ll need to change the code to configure that.
HTTPS, no prefix, port 443
for i in $(seq 1 10); do echo -n "Test $i: "; go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "socks5://$SERVER_MEGAFON|$OUTLINE_SERVER" https://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: 2024/04/29 16:16:13 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: 2024/04/29 16:16:23 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 6: AS14061 DigitalOcean, LLC
Test 7: 2024/04/29 16:16:34 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 8: AS14061 DigitalOcean, LLC
Test 9: 2024/04/29 16:16:42 HTTP request failed: Get "https://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 10: AS14061 DigitalOcean, LLC
HTTP, no prefix, port 443
for i in $(seq 1 10); do echo -n "Test $i: "; go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "socks5://$SERVER_MEGAFON|$OUTLINE_SERVER" http://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: 2024/04/29 16:17:04 HTTP request failed: Get "http://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
HTTPS, TLS prefix, port 443
for i in $(seq 1 10); do echo -n "Test $i: "; go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "socks5://$SERVER_MEGAFON|$OUTLINE_SERVER?prefix=%16%03%01" https://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
HTTP, TLS Prefix, Port 443
$ for i in $(seq 1 10); do echo -n "Test $i: "; go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport "socks5://$SERVER_MEGAFON|$OUTLINE_SERVER?prefix=%16%03%01" http://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: 2024/04/29 16:20:20 HTTP request failed: Get "http://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 5: AS14061 DigitalOcean, LLC
Test 6: 2024/04/29 16:20:32 HTTP request failed: Get "http://ipinfo.io/org": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
exit status 1
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
While the fetch tool doesn’t have a timeout option, you can use our http2transport proxy + curl. I’m now getting more consistent results. I’m not seeing consistent blocking in either Bee Line or Megafon, so I think the timeouts were issues with my remote proxy. Again, it would be great to see direct measurements.
Run the local proxy:
go run github.com/Jigsaw-Code/outline-sdk/x/examples/http2transport@latest -transport "$SERVER_BEELINE|$OUTLINE_SERVER"
2024/04/29 16:42:08 Proxy listening on 127.0.0.1:1080
Then use curl.
Bee Line
HTTP
$ for i in $(seq 1 10); do echo -n "Test $i: "; curl -p -x http://localhost:1080 -sS http://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: curl: (52) Empty reply from server
Test 8: curl: (52) Empty reply from server
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
HTTPS
for i in $(seq 1 10); do echo -n "Test $i: "; curl -p -x http://localhost:1080 -sS https://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
Megafon
$ go run github.com/Jigsaw-Code/outline-sdk/x/examples/http2transport@latest -transport "socks5://$SERVER_MEGAFON|$OUTLINE_SERVER"
2024/04/29 16:47:08 Proxy listening on 127.0.0.1:1080
HTTP
$ for i in $(seq 1 10); do echo -n "Test $i: "; curl -p -x http://localhost:1080 -sS http://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
HTTPS
$ for i in $(seq 1 10); do echo -n "Test $i: "; curl -p -x http://localhost:1080 -sS https://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
MTS
go run github.com/Jigsaw-Code/outline-sdk/x/examples/http2transport@latest -transport "socks5://$SERVER_MTS|$OUTLINE_SERVER"
2024/04/29 16:59:14 Proxy listening on 127.0.0.1:1080
HTTP
$ for i in $(seq 1 10); do echo -n "Test $i: "; curl -p -x http://localhost:1080 -sS http://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: AS14061 DigitalOcean, LLC
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: AS14061 DigitalOcean, LLC
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
HTTPS
$ for i in $(seq 1 10); do echo -n "Test $i: "; curl -p -x http://localhost:1080 -sS https://ipinfo.io/org; done
Test 1: AS14061 DigitalOcean, LLC
Test 2: AS14061 DigitalOcean, LLC
Test 3: AS14061 DigitalOcean, LLC
Test 4: AS14061 DigitalOcean, LLC
Test 5: curl: (56) Failure when receiving data from the peer
Test 6: AS14061 DigitalOcean, LLC
Test 7: AS14061 DigitalOcean, LLC
Test 8: curl: (56) Recv failure: Connection reset by peer
Test 9: AS14061 DigitalOcean, LLC
Test 10: AS14061 DigitalOcean, LLC
Note: Shadowsocks doesn’t communicate TCP resets, so those resets are from the proxy in Russia, not the target website.
Для многочисленных тестов с подключением к одному dest_addr:dest_port возможен выбор src_addr:src_port из уже блокируемой 4-tuple (src_addr, src_port, dest_addr, dest_port). Новое подключение не отменяет блокировку.
It’s Tele2 cellular, Saint Petersburg.
I’ve also tested Beeline, MTS, Megafon and Yota @ Saint Petersburg, all are blocked.
You need to absolutely make sure that your ClientHello is large enough, as curl with mbedtls for example does not add padding extension and it does not hit 411 bytes length needed to trigger the block.
shadowsocks-notblock-yota-28.04.2024.pcapng (105,4 КБ)
Прикрепляю дамп с удачным подключением к серверу Hetzner из Уфы (Yota), подключение к Outline 162.55.42.178:24475 без префикса.
Блокировки прекратились с 30-го апреля на территории Башкортостана и Татарстана по всем провайдерам. Есть клиенты, которые жалуются на подключение с Билайна из Пензы, при этом чистый SS-блочится, а Outline с префиксом ClientHello не блокируется.
This is Outline traffic from opt-in metrics. You can see a gradual decline, supporting a partial block, and then it starts to go back up, aligning with @murka’s statement that blocking stopped on April 30.
Oh, I missed that the 411 bytes was required. With the Outline SDK, we can add a split to the Shadowsocks stream. The Outline Client doesn’t support that yet, but we want to move towards that. Perhaps the client can automatically try different splits if the connection fails.
На 2024-05-05T17:54:00Z блокировки полностью шифрованных протоколов сохраняются на мобильных Теле2, Мегафон, МТС, Билайн и Йота Санкт-Петербург.
Проверял на Shadowsocks, VMESS и собственном генераторе пакетов. Фильтруются все зарубежные направления (Россию не проверял).
Для эксперимента, развернул на московском vps shadowsocks. С мобильного Билайна не работает.
TCP. А UDP проверяли какие-нибудь для интереса?
How did you test Shadowsocks?
I tested Outline Shadowsocks on Tele2, Megafon, MTS and Beeline in St Petersburg, and was not able to observe blocking.
I tested using soax.com, an Outline Server, and the Outline SDK fetch tool. I tried both fetching a HTTPS page and a HTTP page. The HTTPS fetch doesn’t trigger the 411 bytes in the first packet, but the HTTP fetch was done with padding headers to force over 800 bytes in the first packet, and I still couldn’t trigger the block.
5 posts were merged into an existing topic: Обсуждение: неработоспособность ShadowSocks (30.10.2023 +)
A post was merged into an existing topic: Обсуждение: неработоспособность ShadowSocks (30.10.2023 +)
I’m using proxies on a probe (you have access to it) with v2fly configured with shadowsocks over probe’s proxy as an upstream, and sending the requests with regular curl (built with openssl) to HTTPS websites.
HTTP websites indeed do not trigger the block because the filter expects at least two client-server packets with sufficient amount of data (first is ClientHello, second is HTTP request), and HTTP has only one.
Check the PCAP in the top post.
Проверил QUIC (HTTPS-запросами) через Shadowsocks, на этих же каналах (Теле2, Билайн, МТС, Мегафон Санкт-Петербург) блокировки не вижу.
А фильтр проверяет только первые несколько пакетов (как при wireguard блокировках было) или все время за потоком данных следит?
4 posts were merged into an existing topic: Обсуждение: неработоспособность ShadowSocks (30.10.2023 +)
Вроде только начало сессии. Первый (+ возможно, второй) пакет от клиента и как минимум 2 ответных пакета.
I think that pcap was for your random packet generator, given the two packets with exactly 411 bytes.
It would be helpful to see the packets with the Shadowsocks set up.
Whether it triggers is heavily dependent on the implementation, and I have no idea what your set up is doing.
Some implementations will send IV, connect request and application data as 3 separate packets. Some will merge the first two, and some, such as Outline, will merge the 3 of them.
I don’t think the IV+connect reaches 411 bytes, so it shouldn’t trigger the block. Is the pattern detected after the first packet?
It would be really nice to reproduce the blocking with Outline code. I wasn’t able to.
I think the blocking may also be affected by the port number. The servers I tried were on ports 80 and 443, so they may not be affected by this blocking.
The dump in the first message is a real ShadowSocks. V2fly on both server and client.
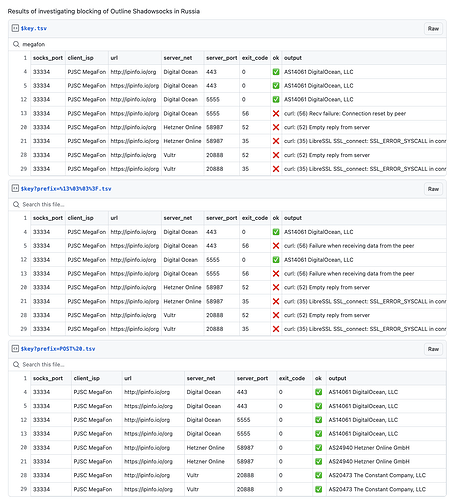
I ran some tests with the Outline SDK, which may work differently than other implementations. It looks like the blocking depends on the location of the server. It also depends on the port number. I was also able to confirm that the initial packet size makes a difference, but only in some ISPs.
- Bee Line seems to be the only one considering the packet size, but only for the Vultr server, not DigitalOcean.
- MTS blocked Shadowsocks access to a server on DigitalOcean, but not Vultr. They are likely using the IP address.
- Blocking on DigitalOcean only happened for the key on port 443. No blocking for the key on the same server, but on port 5555.
- MegaFon blocked Shadowsocks access to a server on Vultr, but not on DigitalOcean. They are likely using the IP address as well.
- The packet size didn’t make a difference for MegaFon and MTS
- Tele2 is not blocking.
Tests
The tests used port 443 for the DigitalOcean server and port 20888 for the Vultr server.
I was not able to reproduce blocking on Tele2. Results for Bee Line depended on the initial packet. Results for MTS and Megafon depended on where the server was.
With a DigitalOcean server and large initial packet (over 800 bytes):
 MTS was consistently timing out
MTS was consistently timing out MegaFon worked most times, with some timeouts. Inconsistent.
MegaFon worked most times, with some timeouts. Inconsistent. Tele2 was consistently working
Tele2 was consistently working Bee Line was consistently working
Bee Line was consistently working
Example:
Using a smaller initial packet didn’t seem to make a difference.
However, when using a key on a different port, 5555, on the same DigitalOcean server, I could consistently connect to the server on all ISPs:
I was also able to connect to the management API on that server, on another high port number.
With a Vultr server and large initial packet:
 MTS was consistently working
MTS was consistently working MegaFon was consistently blocked. Not a timeout. I was getting an EOF from the SOCKS5 service I was using, so the Shadowsocks client probably got a FIN or a RESET.
MegaFon was consistently blocked. Not a timeout. I was getting an EOF from the SOCKS5 service I was using, so the Shadowsocks client probably got a FIN or a RESET. Tele2 was consistently working
Tele2 was consistently working Bee Line was consistently timing out
Bee Line was consistently timing out
Example:
With a Vultr server and small initial packet (300 bytes):
 MTS was consistently working
MTS was consistently working MegaFon was consistently blocked. Not a timeout. I was getting an EOF from the SOCKS5 service I was using, so the Shadowsocks client probably got a FIN or a RESET.
MegaFon was consistently blocked. Not a timeout. I was getting an EOF from the SOCKS5 service I was using, so the Shadowsocks client probably got a FIN or a RESET. Tele2 was consistently working
Tele2 was consistently working Bee Line was consistently working
Bee Line was consistently working
Example:
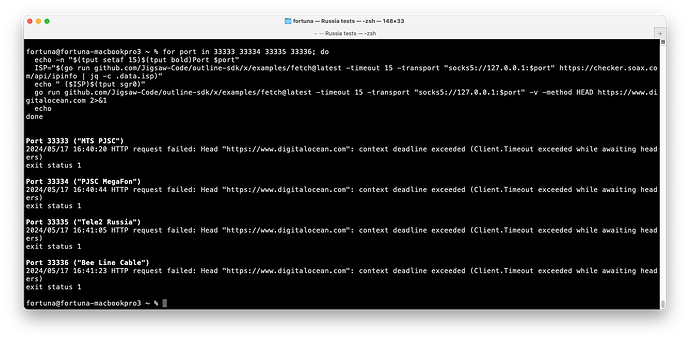
ISPs are targeting specific cloud providers, as reported in April.
I was able to demonstrate that www.digitalocean.com, which runs on Cloudflare, is blocked by SNI. You observe timeouts:
I did manage to successfully fetch the page on Tele2 once.
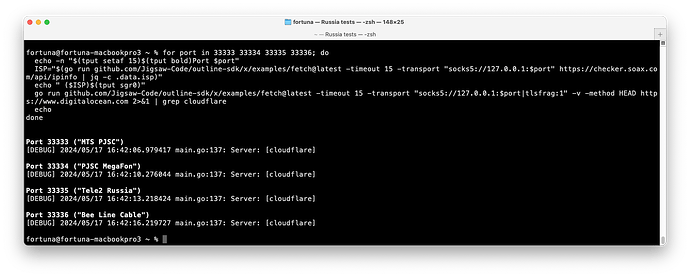
If you use TLS Record Fragmentation, you can successfully, and consistently fetch the page:
3 posts were merged into an existing topic: Обсуждение: неработоспособность ShadowSocks (30.10.2023 +)
Outline SDK fetch tool produces small TLS ClientHello of 329 bytes, the first encrypted Shadowsocks packet is less than 411 bytes, that’s why you don’t see the block.
$ go run github.com/Jigsaw-Code/outline-sdk/x/examples/fetch@latest -transport 'socks5://127.0.0.1:33333|ss://xxx…' https://ifconfig.co
You can use your http2transport + curl to trigger the block.
$ go run github.com/Jigsaw-Code/outline-sdk/x/examples/http2transport@latest -transport 'socks5://127.0.0.1:33333|ss://xxx…' -localAddr 127.0.0.1:44111 &
$ curl -x 127.0.0.1:44111 https://ifconfig.co
curl: (56) Failure when receiving data from the peer
Note that in my tests I was actually fetching HTTP with a padding header to make the first packet larger with -H "Padding: $(printf %800s | tr ' ' 'X')".
I need to check the fetch tool again to make sure the first packet is indeed large. I tested it before with the http2proxy tool and that trick to make the first packet bigger worked after I made a fix to the code (some issue with the HTTP client buffering).
I was actually able to reproduce this same blocking on MTS above. Did you find any inconsistency with my findings?
That doesn’t work, the censor also expects the replies to be of ServerHello/Certificate template based on packet sizes and amount of reply packets.
There should be at least two reply packets for one request packet, and also another request packet.
In other words, the filter expects:
- Client→Server packet with 411+ bytes length (ClientHello)
- Server→Client packet (ServerHello, 100+ bytes of length AFAIK, don’t have notes on hand)
- Another Server→Client packet (Certificate + ServerKeyExchange continuation)
- Client→Server packet (HTTP GET)
Yes — the block is enabled on all cellular operators and all ports.
A post was merged into an existing topic: Обсуждение: неработоспособность ShadowSocks (30.10.2023 +)
So it’s not only the first packet. That is helpful.
I still don’t fully understand the pattern though.
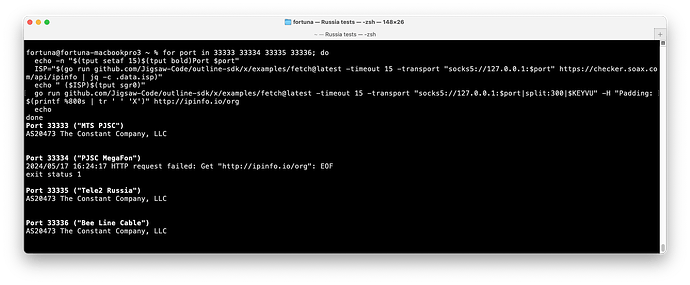
I was able to reproduce the blocking with HTTPS. However, it doesn’t not always happen. DO port 5555 worked on Bee Line and DO port 443 worked on Tele2.
Here are my results:
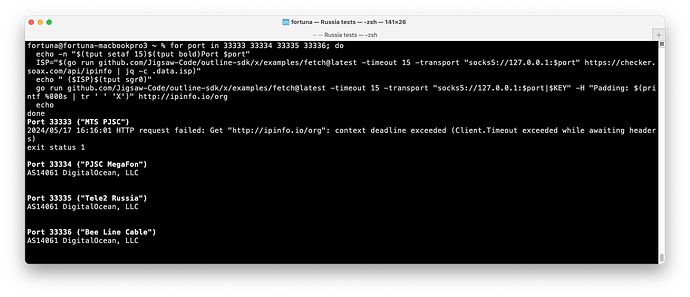
socks_port client_isp url server_net port exit_code ok output
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Operation timed out after 10002 milliseconds with 0 bytes received
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33334 PJSC MegaFon http://ipinfo.io/org Hetzner Online 58987 52 ❌ curl: (52) Empty reply from server
33335 Tele2 Russia http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33336 Bee Line Cable http://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Operation timed out after 10006 milliseconds with 0 bytes received
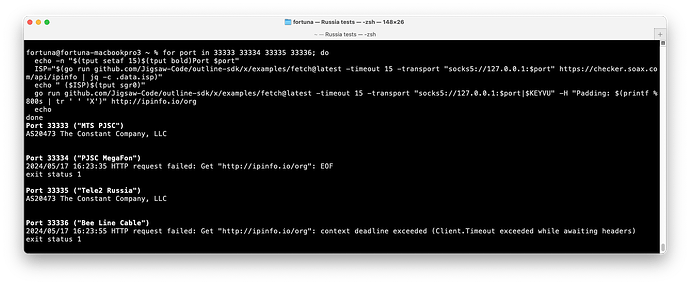
33333 MTS PJSC http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33334 PJSC MegaFon http://ipinfo.io/org Vultr 20888 52 ❌ curl: (52) Empty reply from server
33335 Tele2 Russia http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33336 Bee Line Cable http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Connection timed out after 10005 milliseconds
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Connection timed out after 10005 milliseconds
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 443 56 ❌ curl: (56) Failure when receiving data from the peer
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Failure when receiving data from the peer
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Recv failure: Connection reset by peer
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Failure when receiving data from the peer
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC https://ipinfo.io/org Hetzner Online 58987 56 ❌ curl: (56) Failure when receiving data from the peer
33334 PJSC MegaFon https://ipinfo.io/org Hetzner Online 58987 35 ❌ curl: (35) LibreSSL SSL_connect: SSL_ERROR_SYSCALL in connection to ipinfo.io:443
33335 Tele2 Russia https://ipinfo.io/org Hetzner Online 58987 56 ❌ curl: (56) Recv failure: Connection reset by peer
33336 Bee Line Cable https://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Connection timed out after 10003 milliseconds
33333 MTS PJSC https://ipinfo.io/org Vultr 20888 56 ❌ curl: (56) Failure when receiving data from the peer
33334 PJSC MegaFon https://ipinfo.io/org Vultr 20888 35 ❌ curl: (35) LibreSSL SSL_connect: SSL_ERROR_SYSCALL in connection to ipinfo.io:443
33335 Tele2 Russia https://ipinfo.io/org Vultr 20888 56 ❌ curl: (56) Recv failure: Connection reset by peer
33336 Bee Line Cable https://ipinfo.io/org Vultr 20888 56 ❌ curl: (56) Failure when receiving data from the peer
Here is the script
for socks_port in 33333 33334 33335 33336; do
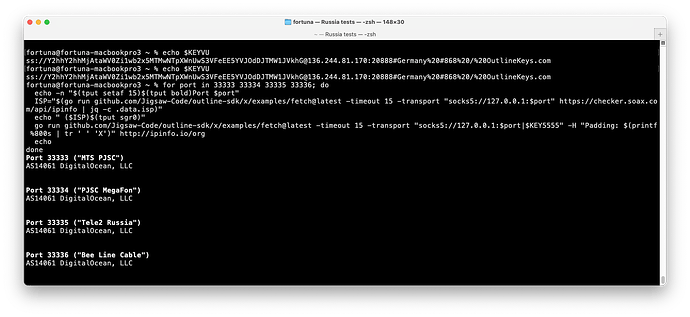
isp="$(curl -s --show-error -p -x 127.0.0.1:1080 --max-time 10 --proxy-header "Transport: socks5://127.0.0.1:$socks_port" https://checker.soax.com/api/ipinfo | jq -r .data.isp)"
for url in http://ipinfo.io/org https://ipinfo.io/org; do
for key in $KEY $KEY5555 $KEY_HETZNER $KEY_VULTR; do
server_net="$(curl -s --show-error -p -x 127.0.0.1:1080 --max-time 10 --proxy-header "Transport: $key" https://checker.soax.com/api/ipinfo | jq -r .data.isp)"
server_port=$(sed -En 's|.*:([0-9]+).*|\1|p'<<< "$key")
output="$(curl -s --show-error -p -x 127.0.0.1:1080 --max-time 10 --proxy-header "Transport: socks5://127.0.0.1:$socks_port|$key" "$url" 2>&1)"
exit_code=$?
if [[ $exit_code == 0 ]]; then
img="✅"
else
img="❌"
fi
echo "$socks_port\t$isp\t$url\t$server_net\t$server_port\t$exit_code\t$img\t$output"
done
done
done | tee table.txt
echo "socks_port\tclient_isp\tserver_net\tserver_port\turl\texit_code\tok\toutput\n$(sort -s -k 3,5 -k 1n -t $'\t' < table.txt)" | column -t -s $'\t'
Note that you can pass the transport to the http2proxy via a HTTP header, so you don’t need to restart it for different transports. I started it with
go run github.com/Jigsaw-Code/outline-sdk/x/examples/http2transport@latest
If I use a simple TCP split on byte 5 (split:5), results are mostly the same, except that a couple more cases are successful with HTTPS (4 vs 2 without the split).
socks_port client_isp url server_net port exit_code ok output
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Operation timed out after 10005 milliseconds with 0 bytes received
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33334 PJSC MegaFon http://ipinfo.io/org Hetzner Online 58987 52 ❌ curl: (52) Empty reply from server
33335 Tele2 Russia http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33336 Bee Line Cable http://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Operation timed out after 10005 milliseconds with 0 bytes received
33333 MTS PJSC http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33334 PJSC MegaFon http://ipinfo.io/org Vultr 20888 52 ❌ curl: (52) Empty reply from server
33335 Tele2 Russia http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33336 Bee Line Cable http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Connection timed out after 10006 milliseconds
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 443 56 ❌ curl: (56) Failure when receiving data from the peer
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Failure when receiving data from the peer
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Failure when receiving data from the peer
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Failure when receiving data from the peer
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Recv failure: Connection reset by peer
33333 MTS PJSC https://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33334 PJSC MegaFon https://ipinfo.io/org Hetzner Online 58987 35 ❌ curl: (35) LibreSSL SSL_connect: SSL_ERROR_SYSCALL in connection to ipinfo.io:443
33335 Tele2 Russia https://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33336 Bee Line Cable https://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Connection timed out after 10003 milliseconds
33333 MTS PJSC https://ipinfo.io/org Vultr 20888 56 ❌ curl: (56) Failure when receiving data from the peer
33334 PJSC MegaFon https://ipinfo.io/org Vultr 20888 35 ❌ curl: (35) LibreSSL SSL_connect: SSL_ERROR_SYSCALL in connection to ipinfo.io:443
33335 Tele2 Russia https://ipinfo.io/org Vultr 20888 56 ❌ curl: (56) Failure when receiving data from the peer
33336 Bee Line Cable https://ipinfo.io/org Vultr 20888 56 ❌ curl: (56) Recv failure: Connection reset by peer
Prefixes seem to really help.
Using POST%20, almost all connections succeeded. Tele2 was completely successful. Megafon had only one HTTP timeout with DigitalOcean 443. On MTS, HTTP and HTTPS timed out with DigitalOcean 443. On Bee Line HTTP and HTTP timed out on Hetzner.
This reinforces that the blocking is based on random-looking traffic.
Results, sorted by ISP, server network and port:
socks_port client_isp url server_net port exit_code ok output
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Operation timed out after 10006 milliseconds with 0 bytes received
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Connection timed out after 10005 milliseconds
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33333 MTS PJSC https://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33333 MTS PJSC http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33333 MTS PJSC https://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Operation timed out after 10003 milliseconds with 0 bytes received
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33334 PJSC MegaFon http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33334 PJSC MegaFon https://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33334 PJSC MegaFon http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33334 PJSC MegaFon https://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33335 Tele2 Russia https://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33335 Tele2 Russia http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33335 Tele2 Russia https://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable http://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Operation timed out after 10003 milliseconds with 0 bytes received
33336 Bee Line Cable https://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Connection timed out after 10003 milliseconds
33336 Bee Line Cable http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33336 Bee Line Cable https://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
I got the exact same results when using a TLS prefix that looks like a fragmented record ( %16%03%01%00%C2%A8%01%01).
When using the DNS over TCP prefix (%05%C3%9C_%C3%A0%01%20), the results were worse, but still better than no prefix. It seems it triggered the HTTPS blocking in some cases, but not all cases. This can help figure out the detection rules.
Results:
socks_port client_isp url server_net port exit_code ok output
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Operation timed out after 10005 milliseconds with 0 bytes received
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 443 28 ❌ curl: (28) Connection timed out after 10004 milliseconds
33333 MTS PJSC http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC https://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33333 MTS PJSC http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33333 MTS PJSC https://ipinfo.io/org Hetzner Online 58987 56 ❌ curl: (56) Failure when receiving data from the peer
33333 MTS PJSC http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33333 MTS PJSC https://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 443 56 ❌ curl: (56) Failure when receiving data from the peer
33334 PJSC MegaFon http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33334 PJSC MegaFon https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Recv failure: Connection reset by peer
33334 PJSC MegaFon http://ipinfo.io/org Hetzner Online 58987 52 ❌ curl: (52) Empty reply from server
33334 PJSC MegaFon https://ipinfo.io/org Hetzner Online 58987 35 ❌ curl: (35) LibreSSL SSL_connect: SSL_ERROR_SYSCALL in connection to ipinfo.io:443
33334 PJSC MegaFon http://ipinfo.io/org Vultr 20888 52 ❌ curl: (52) Empty reply from server
33334 PJSC MegaFon https://ipinfo.io/org Vultr 20888 35 ❌ curl: (35) LibreSSL SSL_connect: SSL_ERROR_SYSCALL in connection to ipinfo.io:443
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 443 56 ❌ curl: (56) Failure when receiving data from the peer
33335 Tele2 Russia http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33335 Tele2 Russia https://ipinfo.io/org Digital Ocean 5555 56 ❌ curl: (56) Failure when receiving data from the peer
33335 Tele2 Russia http://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33335 Tele2 Russia https://ipinfo.io/org Hetzner Online 58987 0 ✅ AS24940 Hetzner Online GmbH
33335 Tele2 Russia http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33335 Tele2 Russia https://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 443 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 443 56 ❌ curl: (56) Failure when receiving data from the peer
33336 Bee Line Cable http://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable https://ipinfo.io/org Digital Ocean 5555 0 ✅ AS14061 DigitalOcean, LLC
33336 Bee Line Cable http://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Operation timed out after 10001 milliseconds with 0 bytes received
33336 Bee Line Cable https://ipinfo.io/org Hetzner Online 58987 28 ❌ curl: (28) Connection timed out after 10002 milliseconds
33336 Bee Line Cable http://ipinfo.io/org Vultr 20888 0 ✅ AS20473 The Constant Company, LLC
33336 Bee Line Cable https://ipinfo.io/org Vultr 20888 56 ❌ curl: (56) Failure when receiving data from the peer
I also tried using the POST%20 prefix and it worked. ISP: Tattelecom.
FY, I put the results on the following Gist, which allow you to more easily see all the results and filter by ISP, server network, HTTPS, etc:
had similar symptoms on Tele2 about a month ago, fixed by enabling v2ray plugin
Here is a better dataset with all the measurements in one table:
And here is the decision tree based on that dataset that characterizes the blocking (open in a new tab):
Судя по
блок мешающий работе SS откатили. На T2 так же работает, подтверждаю
И снова включили, поведение аналогичное, с N-го раза ресурсы открываются.
Сегодня днем проявилось на проводном ЭрТелеком, сайты открываются с четвертого-пятого пинка. В telegram текстовые сообщения идут без проблем, но тормозит загрузка медиа.
Перешла на VLESS пока, с ним все хорошо.
На мобильных операторах у меня не проявляется, но теперь проявляется на:
| ISP | AS | Location |
|---|---|---|
| Rostelecom | AS12389 | Orenburg |
| JSC Ufanet | AS60095 | Nizhny Novgorod |
| Rostelecom | AS12389 | Perm region |
A post was merged into an existing topic: Обсуждение: неработоспособность ShadowSocks (30.10.2023 +)
Днем на проводном эртелеком: SS и SS2022, nekoray под windows, hiddify next на дебиане и hiddify next на андроид (через вайфай) - до двух разных серверов на digital ocean (мой и коллеги). На серверах xray, поднятый по инструкции с хабра. Взяла первый попавшийся рабочий носок с 4пда - та же картина, вроде работает, но через три раза на четвертый, так что вроде блок не по хостингу только.
Вечером на проводном Ростелеком: те же клиенты, тот же сервак (уже только мой). SS не пашет, VLESS (xtls-REALITY) нормально.
Регион Нижний Новгород
Да, на мобильных SS на высоких портах продолжал работать все это время
A post was merged into an existing topic: Обсуждение: неработоспособность ShadowSocks (30.10.2023 +)
| ISP | AS | Location |
|---|---|---|
| JSC Ufanet | AS24955 | Republic of Bashkortostan |
Начали блокировать сегодня. При чем пытаются дропать соединение присылая в ответ [RST, ACK]. Но и настоящий ответ при этом не приходит. Тип шифра кажется значения не имеет.
Dpidetector в принципе эту информацию подтверждает. Соединение пока что пробивается с нескольких попыток.
Здравствуйте)
Кемерово, МТС, замедлен до неработоспособности чистый SS-2022, телега тоже, ощущение, что начали “замедлять” все, что не могут распознать. Xtls-reality c VLESS на той же впске работает отлично.
Существует и применяется 2 техники блокировок/замедлений разных протоколов и vpn:
- распознавание на лету и принятие решения
- то, что быстро не распозналось на лету как обычные протоколы - попадает в список, откуда потом производится сканирование ендпоинта, куда раньше ходили - и если распознается какой либо вид vpn или протокол на той стороне - сразу блочится ip или port.
вторая - самая неприятная блокировка. к ней все и движется. отсюда вы наблюдаете “начало работать” “перестало работать”. То есть они просто обходят ваши vpn ендпоинты потом и блочат.
В виду всех этих тенденций нужно приступать к разработке обертки протокола vpn с полной эмуляцией другого легитимного протокола. Скажем outline на 443 нужно научить работать как обычный веб сервер ДО определенных кондиций со второны клиента. Например: после 3го get запроса 4й должен быть определенным и тогда сервер перейдет от эмуляции nginx на shadowsocks.
тоже самое с другими протоколами.
иными словами, приближается время когда нужно будет заканчивать борьбу за нераспознаваемость протоколов, и начинать борьбу за ложную распознаваемость, мимикрию. потому что они перейдут к тактике “замедлять всё что не можем распознать”. Нужно делать так что бы распознали.
Мегафон. Блокируют ноды obfs4
obfs4_block.pcapng (757,9 КБ)
не по ip а конкретно протокол
snowflake тоже не работает. Все также проходят несколько пакетов DTLS и зависание
Ничего удивительного. obfs4 выглядит как random, так же как shadowsocks, который давно режут на мобильном интернете. И раньше obfs4 покашливал в лог.
Могу посоветовать забутстрапить tor через чистый интернет и быстро переключиться на obsf4 (чтобы был горячий запуск). Т.к. по наблюдениям секут только bootstrap по размерам пакетов openssl.
и чтото с этим планируется делать?. obfs4 позиционировали себя как супер-пупер протокол который никогда не заблокируют. А теперь оказывается у фашистких режимов есть вполне действующие средства.
obfs4 слабенький протокол, режется белым списком протоколов. Попробуйте другие более современные, которые маскируются под разрешённые.
какой snowflake так же не работает
webtunnel попробуйте.
Ему уже 10 лет. Тогда он был расчитан на то что неизвестный и до того как цензоры в китае научились блочить нойз. Это сам факт нойза. “Не правильно ведешь себя в тюрьме, слишком вызывающе ходишь. Зэки тебя нагнут если не наденешь ватник.”
Сам разраб сказал что obfs4 говно. Даже ванильные мосты сейчас лучше работают.
ванильные мосты работают ровно 1 час. Они их блочат по ip
webtunnel вообще не работает
Сам фронт мог войти в оффлайн, донеры же не будут гонять эти мосты постоянно (и слава богу) там ротация может быть, особенно если они видят что траффик больше не идет = заблочились. Ты дигом и курлом проверь домен сначала.
На проводных провайдерах ничего не блокируют. блокировка конкретно тор идет с мегафона и мтс
Да, серьёзно за tor взялись. Но оно и понятно, в голове тех, кто затевает блокировки, это самый популярный шпионский инструмент ![]() . Ну, попробуйте yggdrasil мосты.
. Ну, попробуйте yggdrasil мосты.
у меня симки мтс мегафон
На мобильных очень не любят webrtc из-за разговорного траффика. Тор тут не причем. Тариф при том
тоесть о тупо рубят webrtc трафик?
но obfs4 работают по другому протоколу
Могут как и битторрент. Для них траффик как золото, они на нем выгоду везде ищут. Даже с безлимитами будут тебя замедлять
здесь уже ответили что obfs4 это говно
фашисткие режимы нам не дадут свободно общатся
Мосты как блокируются, так и разблокируются - постоянно. Я пользуюсь на паре инсталляций tor-relay-scanner, который раз в час-два подкидывает три десятка свежих обычных доступных релеев в конфиг torrc на маршрутизаторе. Работает с 2022-го года без каких-либо телодвижений, буквально zero maintenance.
webtunnel отлично работает - другое дело, что мосты достаточно быстро мрут, и их в целом немного. У меня на мобиле работает без каких-либо проблем, и бутстрапится исключительно быстро. В конфиг насыпано ~10 разных мостов.
В некоторых странах, например Саудовской Аравии, ОАЭ тоже режут webrtc, чтобы звонили через оператора или с разрешённых платных местных сервисов.
конфирурацию для webtunnel сообщи я попробую
torrc
https://bridges.torproject.org/options или http://yq5jjvr7drkjrelzhut7kgclfuro65jjlivyzfmxiq2kyv5lickrl4qd.onion/options в помощь.
Выбираете там вариант “webtunnel” в ниспадающем списке, забираете два моста, вставляете в список мостов в мобильном или десктопном приложении.
На десктопе: Settings → Connection → Bridges → Add new bridges
На андроиде: Configure connection → Config Bridge → Use a Bridge → Provide a Bridge I know
CLI-клиент:
UseBridges 1
ClientTransportPlugin webtunnel exec <абсолютный путь до бинарника client>
Bridge <строка с адресом и параметрами моста, как есть с bridges.torproject.org для варианта webtunnel>
На каждый мост - новая строка “Bridge”.
вы мне предлогаете ipv6. IPv6 он есть но там очень серьзные тормоза. там весь травфик идет через брокера
Нет. Эти мосты абсолютно нормально работают через IPv4.
Yota. Snowflake перестал работать где-то пару дней назад. Клиент посылает оферы без ответа. Перенастроил на использование AMP cache – работает как и прежде. На торовском форуме не нашёл новости что брокер не работает, возможно какие-то блокировки в сторону cdn77.com.
Похоже со сноуфлейком действительно что-то не то. Snowflake partially blocked in Russia 2024-11 (#40407) · Issues · The Tor Project / Anti-censorship / Pluggable Transports / Snowflake · GitLab
Сегодня ночью в логе моего демона так же обнажил что целый час демон давал stale connections.
log
offer created
broker rendezvous peer received
connected
через ровно 20 секунд
trying a new proxy: no messages received, closing stale connection
Но мне кажется они добъют тор не этим, а убив брокеров после запрета всех сдн.
Йота. Много ретрансмиссий, но всё-же соединяется неспеша.
Есть у кого-нибудь свежая информация по рабочим префиксам + портам на ShadowSocks (Outline VPN) ?